ASIS Westchester was a recent recipient of a phishing email attack. The simple method used was not very high tech, and it indicates that many non-profits and other organizations may be vulnerable to similar attacks.
This incident was not a traditional “phishing” email as it was not asking for credit card information or other personal info, and it was not asking to “click a link” that would download malware, it was just asking for money.
Here’s what happened:
The treasurer of our ASIS Westchester NY chapter was recently contacted by email from a fraudster claiming to be me, Charles Patterson, the chapter chairman. Like many organizations, the names and contact email addresses of our board, including the chairman and treasurer, are posted on our website. This makes it easy for someone to create such a spoof.
The original email was sent to the treasurer’s email address posted on our website, using our website url, “treasurer@asiswestchester.org”. This email address is only used for receiving public emails that will get forwarded to the treasurer’s actual email address.
The first email received was just a request to elicit a reply to find out if the treasurer would be able to make an urgent payment to a supposed “vendor”.
Hi —— ———,
How are you today? I will need you to process check payment to a vendor and have it mailed overnight, kindly let me know if this is convenient for you at the moment so I can forward the information
Your swift response will be appreciated.
Thanks
Our treasurer recognized that the “from” email address, although it had my name, was not my usual email address, and the greeting also addressed him in an oddly formal way that was not typical of our communications.
After our treasurer contacted me through other channels we realized that this was a scam email. He replied to the email simply asking for “more information”. This is where the fraud gets interesting. An answer came back asking him to send a check, overnight, for $2150 to a specific name and address.
Here is the information for the payment, issue the check in the vendors name and have it mailed overnight to the address.
Name: D——- W—— A——-
Address: ———-, Xenia,Ohio 45385
Amount: $2,150.00
Immediately the check is sent do get back to me with the tracking number and overnight shipment service used.
Thanks
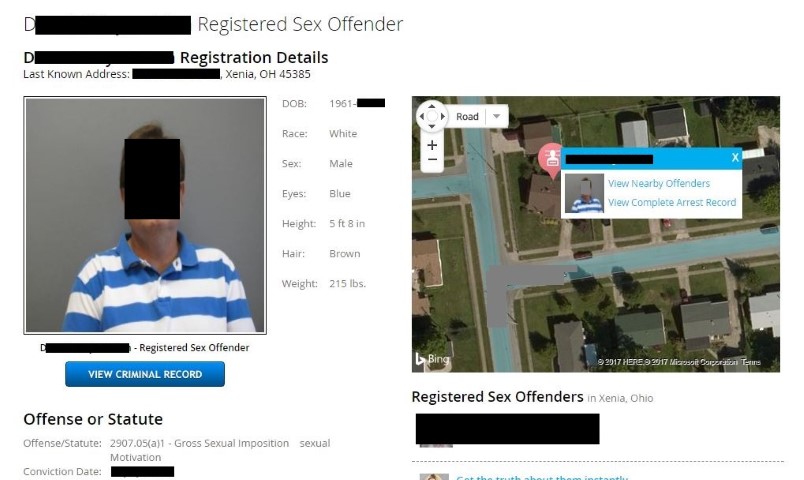
A Google search of the name and address revealed that it was the last known address of a registered sex offender in Xenia, Ohio.
Here are some points worth noting regarding this situation:
- The vulnerability was that our website, as do many company and organization sites, displays the names of our board (including chairman and treasurer) along with an email addresses for each, so this information is easy to find. The email addresses on the website are not our actual personal or work email addresses, though; they are set up as public facing addresses using the organization url, so as to not reveal personal addresses.
- Our treasurer recognized the email he received did not appear as our normal email communications would. First, the email address sent to used the organization url, normally that is only from an online contact. We usually communicate using our personal or work addresses. Secondly, he also realized that the “from” address, even though it used my name, was not an email address I had ever used.
- The first email was just probing to find a vulnerable victim, as it did not ask for any money at that time. The second email supplied a name and address but claimed it was a “vendor”, yet it was just a personal name.
- Googling the name and address of the supposed “vendor” provided a good indication that the email was a scam. Not only was it just a residential address, but the name also showed up as a registered sex offender. This person may just be being used by the scammers as a contact for receiving payment. He may have thought he was just participating in a simple money-making scheme, only needing to forward payments on to the real criminals. If he was actually the one behind the scam, he would be quite stupid to use his real name and address – especially as a registered sex offender – although no one says criminals need to be smart.
- There was no request to “click on a link” or other typical phishing or malware attack. Payment was requested through normal mail or other overnight delivery service.
ASIS headquarters had sent out a notice a number of months ago informing chapters that similar emails had been sent to other chapters and that we should be on the lookout for such fraud attempts.
The FBI has been contacted regarding this incident, but due to the number of calls they receive, internet related complaints can only be filed at an online web page. We have yet to hear back from them. We have also reached out to Xenia Police Department to let them know of the incident.
Any organization or company that has names and email addresses of their board, directors, or department heads posted on their website could fall victim to this type of fraud… this includes almost everyone.
If you are responsible for finances for your company or organization, be extra vigilant regarding any such requests for payment.
